Configuring SPF, DKIM and DMARC with Microsoft 365 / Exchange Online

I felt that a simple post on how to implement SPF, DKIM and DMARC is warranted as a first blog post. I will be focusing here on implementing it with Exchange Online environment, so if you are a small, medium or even large business, this guide can get in you the right direction.
For larger organizations, think of this blog post as a good place to start and configure DMARC first to get reports about services sending mail in your name.
❓What are SPF, DKIM and DMARC? Why would I care?
By default anyone can send email on your behalf and email servers do not know if they are legitimately coming from you or not. To this purpose, SPF, DKIM and DMARC are used.
SPF: a statement which tells receiving email servers who can send email on your behalf. For example, I can declare that only Exchange Online can send email on behalf of alesec.com. It's like a bouncer checking that you are on the list (of approved senders) if you are a sending email server.
DKIM: publishing my email's digital signature online publicly and signing outgoing messages going forward. Receiving email server can verify the signature to make sure the message is authentic. It's like the same bouncer verifying your credentials.
🤔 What if the messages do not fulfill SPF and/or DKIM? DMARC to solve the issue
It is up to the default policies at the receiving end to decide what happens to your message if it somehow does not meet SPF or DKIM policy you have placed. To enforce what you want to happen if they fail, you need to use DMARC.
DMARC is simply a policy that tells receiving email address what to do when the message origin or authenticity cannot be verified. The best, most strict policy in DMARC is to simply reject all messages that do not meet all both SPF and DKIM policies, but you can configure it to be more forgiving (not recommended).
DMARC is like telling a bouncer what to do if people are not on the list and don't have the credentials to prove themselves.
🛠️ Implementing
SPF
To configure SPF, only a DNS record is needed. Specifically, a "TXT" record needs to be created in your DNS provider's console. For example, I am using GoDaddy, so I created a new DNS record using their console at https://godaddy.com.
In the console, I double-checked that a similar DNS record does not already exist, and then I created a new TXT record to alesec.com with a TTL 3600 like so:
v=spf1 include:spf.protection.outlook.com -all
Policy basically states the following things:
- Version: SPF1
- Include Exchange Online servers to be allowed to send email on my behalf
- All messages must follow this policy ("-all"). (should would be "~all")
Please note that the policy above only applies to Exchange Online (Microsoft 365) as the mail service. If I had any other services sending email in my organization's name, I would add them to the list. For example, if I sent newsletters via MailChimp, I would need to follow MailChimps guide to implement SPF and add "include:servers.mscv.net" to my SPF policy like so:
v=spf1 include:spf.protection.outlook.com include:servers.mscv.net -all
DKIM
DKIM requires you to set up your email service (in this case Exchange Online) to sign the messages with DKIM. Based on that, DKIM records are published to DNS.
To set DKIM up for Exchange Online you need to go to Microsoft 365 Defender portal https://security.microsoft.com/authentication?viewid=DKIM and enable signing messages for the domain(s) you own.
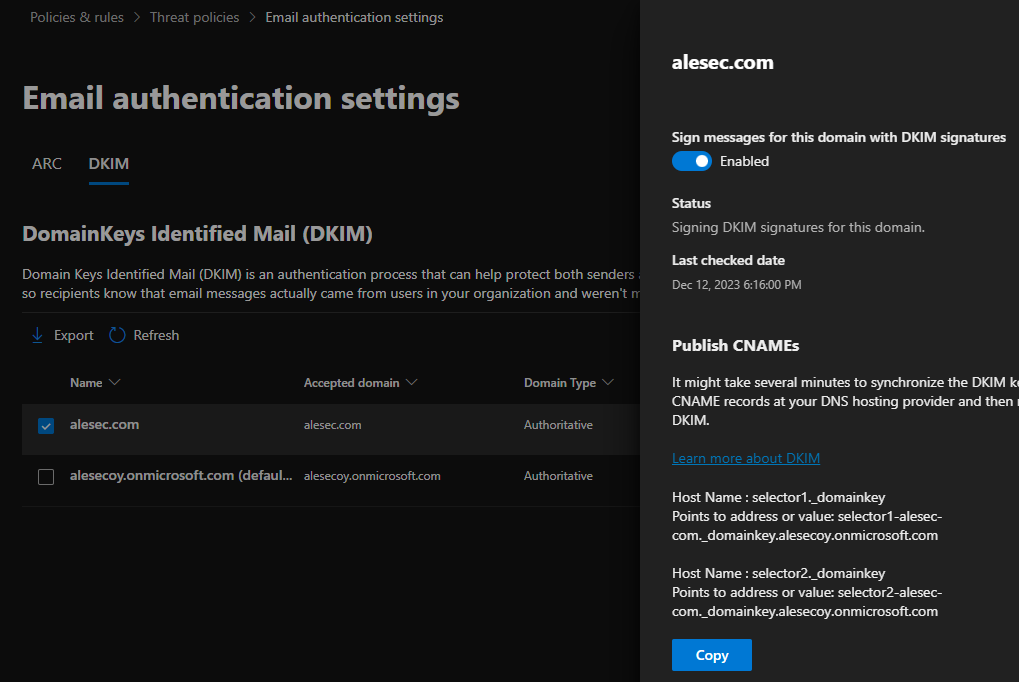
By itself, enabling the feature only toggles on the feature to sign outgoing email messages but there is no way for the receiving server to verify the authenticity. For this, I need to publish the DNS records.
As pointed out in the photo above, I need to create CNAME records on my DNS service to point to Microsoft provided values. In practice, I need to set up the following two records on my DNS:
CNAME selector1.domainkey.alesec.com
selector1-alesec-com._domainkey.alesecoy.onmicrosoft.com
CNAME selector2.domainkey.alesec.com
selector2-alesec-com._domainkey.alesecoy.onmicrosoft.com
Again, if I had other email services sending mail on my organization's behalf (like MailChimp), I would need to follow their guidance and setup and add their DKIM records to DNS too. For example MailChimp: https://dmarcly.com/blog/how-to-set-up-spf-and-dkim-for-mailchimp
DMARC
Like SPF, DMARC only requires setting up a DNS record. Specifically, a TXT record needs to be set up for subdomain "_dmarc". In practice, the TXT record should look like this for "_dmarc.alesec.com":
v=DMARC1; p=reject; sp=reject; ruf=mailto:[email protected]; rua=mailto:[email protected]
DMARC policy basically tells:
- that all messages failing any part of SPF or DKIM should be rejected
- ruf tells where forensic reports of failed received emails should be sent to (by the receiving email server)
- rua tells where the aggregated reports of failed received emails should be sent to (by the receiving email server)
I am not currently using a third-party DMARC service to provide reports about DMARC mails (they are not human readable) but I highly recommend having one! There are lots of providers such as DMARCIAN, EasyDMARC, DMARC Report, Valimail etc.
✅ Verify the configuration
You can easily check the configuration with the following lines at the command line:
SPF:
nslookup -type=TXT alesec.com
DKIM:
nslookup selector1.domainkey.alesec.com
DMARC:
nslookup -type=TXT _dmarc.alesec.com
If you get back your configured policy as a result for each of the commands, everything is in order.
Alternatively, you can use a checker tool like DMARCIAN's Domain Checker, which shows you if you have implemented SPF, DKIM and DMARC correctly:

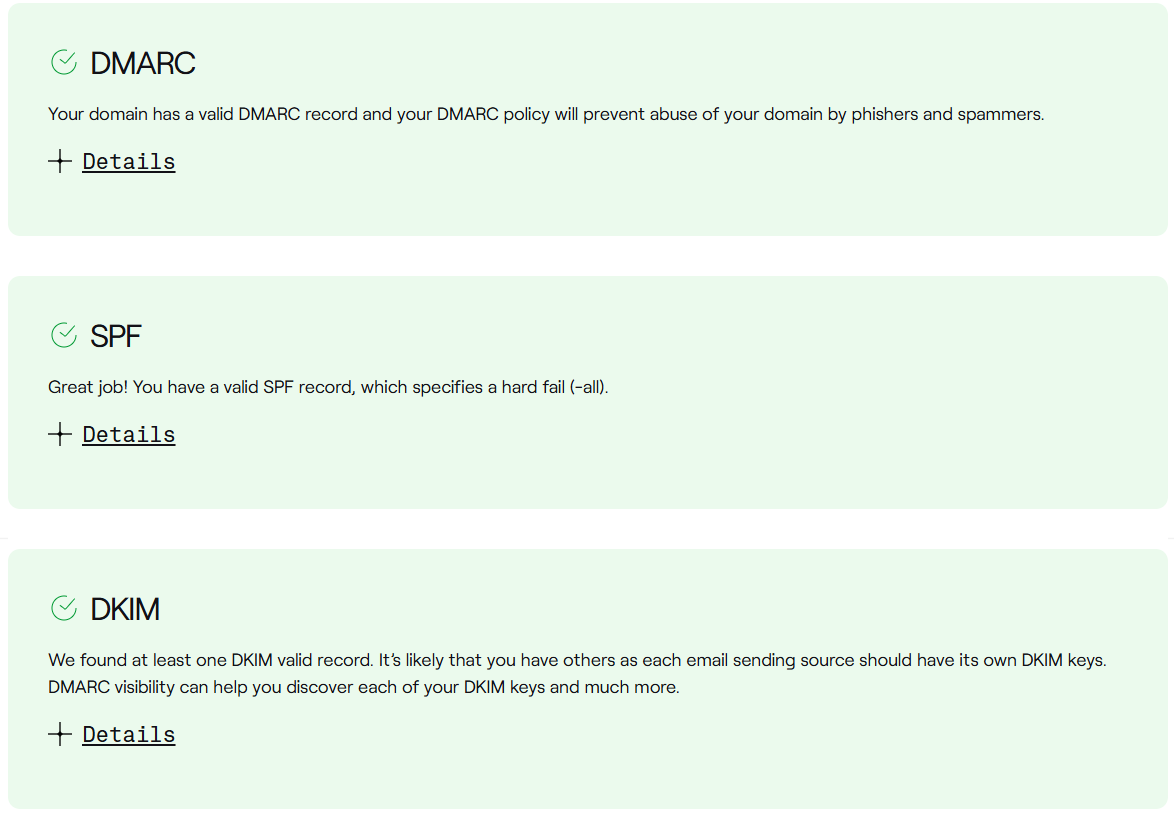
Next steps
In addition to SPF, DKIM and DMARC there are a few things that can boost your email security: BIMI, MTA-STS, SMTP DANE (with DNSSEC) and TLS enforcement but I'll blog about those in a later blog post.
Note that it is recommended best practice to set up at least SPF policy for subdomains too, even if they don't exist. See Microsoft's email authentication guide for more information (link below).
Additional resources
MXToolbox: super nice lookup tool
Microsoft resources for email authentication:



